While reverse engineer Android apps it’s relatively common to perform dynamic analysis in conjunction to static analysis in order to gain runtime information of the app.
There are many ways to get this information from 3rd party apps
- Use Frida hooks to print function arguments
- Patch the app to be debuggable
- Patch the app to log the sensitive information
The above methods have several flaws, Frida is only able to hook a specific function either before or after the function, and poaching apps is relatively complex and almost always causes bugs in the app.
Also many packers / malwares detect modified APKs and crash to intentionally make analysis harder.
Better Solutions for Debugging 3rd Party Android Apps
I’m a big fan of the Android Studio Debugger (JDWP under the hood), as you can easily setup breakpoints, modify the code and even add logic to it, all at runtime, from your favorite IDE.
Sadly, in order to do so you must recompile apps, and that has a high probability of failure.
As my device is rooted and highly customized I decided to find a way to make all apps debuggable.
AOSP Research
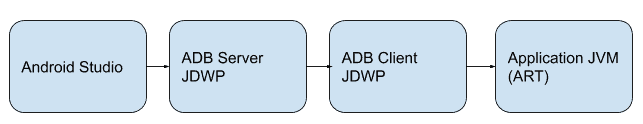
In order to debug an app Android Studio communicates with the App using JDWP over ADB communication as the very high level chart shows:
If you are interested in more depth explanation of the implementation it’s your lucky day, because for some reason, someone from the AOSP guys wrote a pretty decent domcatuion at
/system/core/adb/jdwp_service.cpp
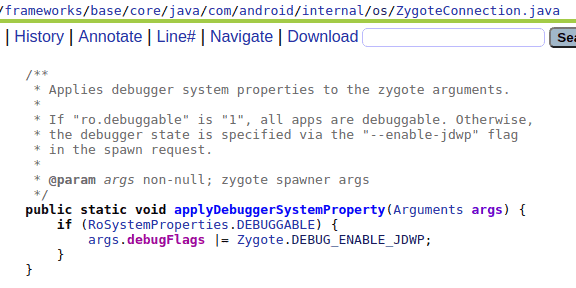
Further research of the AOSP revealed the
That if set as a flag for zygote when initializing a new app, will make the app debuggable.
More interesting is the function “applyDebuggerSystemProperty”
Apparently there is already a support for my debugging needs and all I need to do is to set the ro.debuggable system property to 1.
Modifying the Boot Image
Apparently all ro.* system properties are under the device boot image and can’t be set using the standard “adb shell setprop” command.
Also remount alone won’t do the trick.
There are device specific methods on how to flash modified boot images but most of them are not simple and require relatively large amounts of Android Boot process knowledge.
I decided to find an easier approach and luckily for me someone already built a magisk module that does exactly this
Hidden Settings
Install it and you can modify the property from adb shell.
Also from Android 10 and above system-as-root is implemented so you can just change to ro.* system properties using mounts
mount -o rw,remount /
vi /default.prop
# replace ro.debuggable=0 to ro.debuggable=1 in /default.prop
reboot
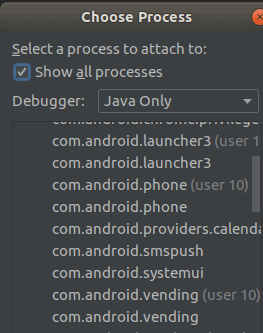
Debugging
Everything is debuggable now – just use “attach debugger” (use Java only otherwise it fails)!
If you want to debug smali and not Java files – use this plugin:
https://github.com/JesusFreke/smalidea
Want to Hear More?
A free consulting meeting included.