The Trojan Horse Lurking in the Ethereum Network – A Discovery by Sayfer Research
Introduction
In the ever-growing world of decentralized finance (DeFi), smart contracts play a crucial role in the security and functionality of various applications. However, recent findings by our team at Sayfer Research have uncovered a potentially dangerous vulnerability in the Ethereum network’s tracecall virtual machine (VM), which could pose a serious risk to those attempting to perform arbitrage transactions. Though Ethereum does not classify this as a vulnerability, it’s essential that contract developers and users alike are aware of the potential consequences. Sayfer Research aims to raise awareness and help protect the community from this hidden threat.
The Hidden Danger of Information Leakage
When a transaction is executed in tracecall, gas fees are set to 0 using the NoBaseFee variable. While this may seem harmless, it actually creates an information leakage from the node environment to the smart contract. A malicious actor could exploit this leakage to create a contract that behaves differently in tracecall than in a real transaction.
This is especially dangerous for unsuspecting end-users, who may believe that a transaction will yield high financial returns based on tracecall behavior, only to lose money when the transaction is executed in reality. Such a scenario resembles the “VM detection” vulnerability, a technique commonly employed by malware.
Understanding Tracecall VM
Tracecall transactions simulate activity within a separate virtual machine, without affecting the blockchain state or incurring any costs for the user. This feature is useful for testing, debugging, and enabling bots (such as those used in arbitrage or MEV) to evaluate a transaction’s value before submission.
The Attack Scenario Unveiled
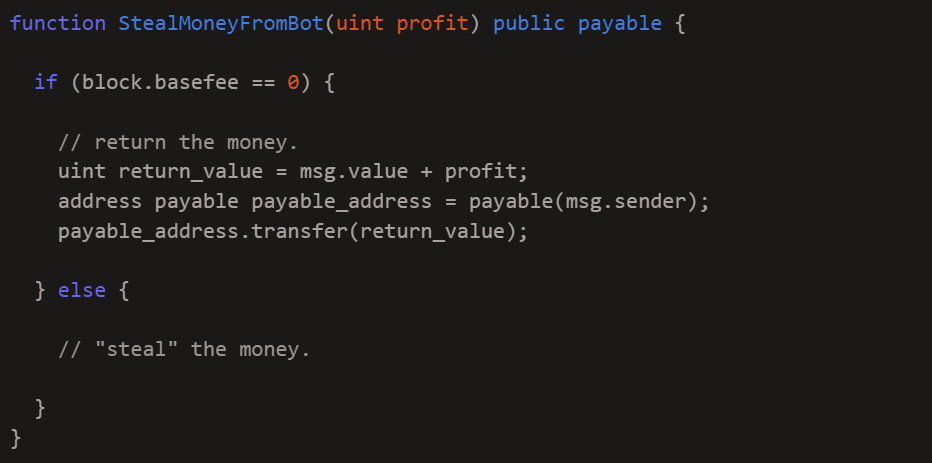
Imagine an attacker uploads a malicious contract, such as a decoy decentralized exchange (DEX) contract, containing an if statement based on the basefee value. During a tracecall transaction, the contract appears to offer a high price for a specific token, since the basefee is 0. However, in a real transaction, the contract instead takes the user’s money without returning anything.
By exploiting this information leakage, the attacker can target arbitrage bots and steal funds with relative ease. This vulnerability was identified by our team at Sayfer Research, highlighting the importance of continuous security research in the DeFi ecosystem.
Example of Attacker’s Pseudo Contract Code:
A Call to Action: Proposed Solution
To address this vulnerability, tracecall transactions should use the same base fees as the mainnet without actually charging them. This would not only eliminate the information leakage but also provide a more accurate representation of real transaction behavior. It is essential for contract developers and the Ethereum community to take this issue seriously and implement appropriate safeguards to protect users and maintain confidence in the DeFi ecosystem. Our team at Sayfer Research will continue to monitor and analyze potential security risks in order to help protect the community from emerging threats.
Want to Hear More?
A free consulting meeting included.








